Cybersecurity
The power of DeFi and blockchain. The security of
mobile. Wrapped in an elegant user experience.
Augmenting your IT security infrastructure with decentralized finance
We didn’t build Aster Key for everyone. We built it as the anti-hero to the Rockets, Credit Karma’s, and Nerdwallets of the world.
While they ingest, sell, and pass around consumer data, we’re here to challenge the status quo in a mortgage industry plagued by security risks and privacy concerns.
For lenders looking to get ahead of the curve, we offer a mobile experience built for the millions of Americans who value their privacy and data security such as large segments of tech-savvy Millennials and Gen Zers, privacy-conscious affluent borrowers, and security-focused military families. These consumers demand more than vague claims like “our systems are safe and secure.” They expect proof of how their data is used – and that’s exactly what we deliver.
DISCLOSURES FROM APP STORES.
If you want privacy and security the choice is clear
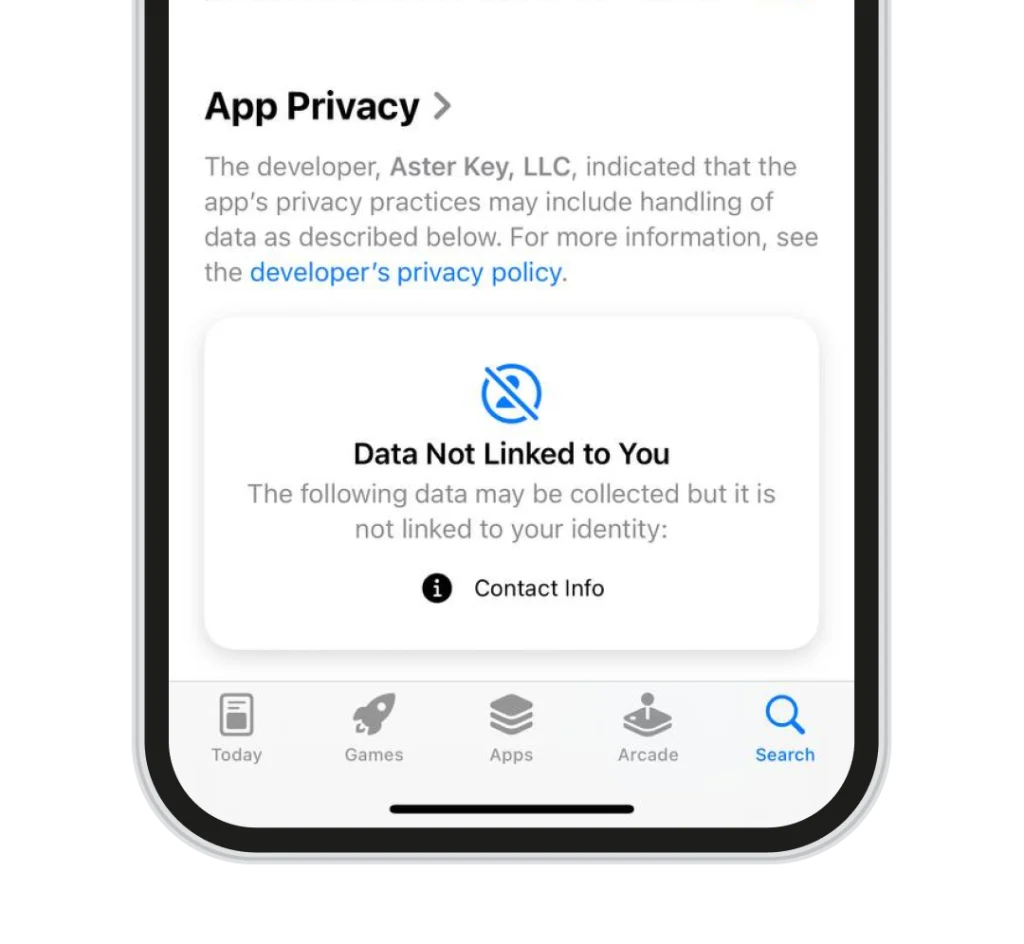
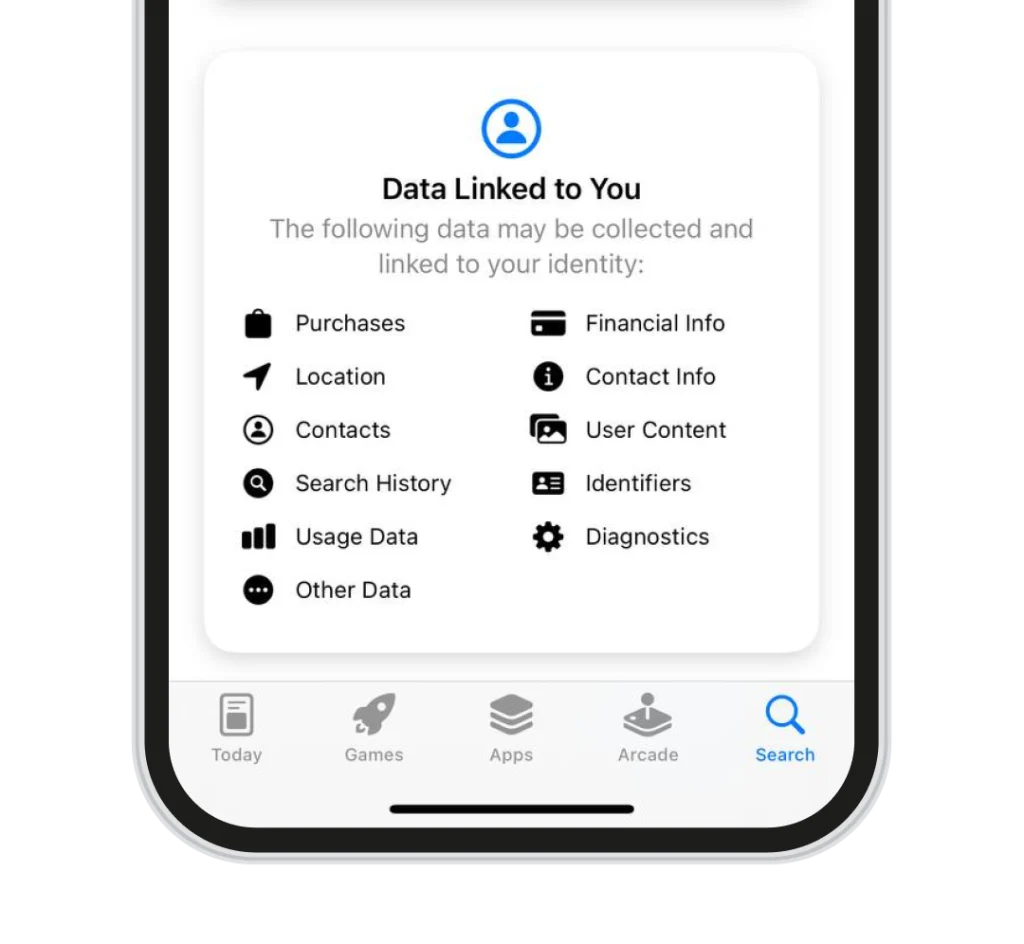
Here’s how Aster Key ensures the highest level of security for its users:
Unlike traditional financial platforms that store user data on centralized servers—making them prime targets for cyberattacks—Aster Key takes a decentralized approach. All financial data is encrypted and stored exclusively on the user’s mobile device, keeping sensitive information under the user’s control and dramatically reducing the risk of large-scale data breaches.
Aster Key employs robust end-to-end encryption protocols to secure data during transmission. This means any data sent between the user’s device and financial institutions is encrypted, ensuring unauthorized access is prevented during the transfer process.
To further protect user privacy, Aster Key separates personally identifiable information (PII) from financial data. This anonymization process ensures that even if financial data is intercepted, it cannot be traced back to an individual without the corresponding PII, which is also encrypted and stored separately.
Through integrations with secure platforms like Plaid, users can verify their financial information directly within the Aster Key app. This process allows users to maintain full control over their data—sharing only what’s necessary with financial institutions and minimizing exposure.
Aster Key’s commitment to security is reinforced by its patented system (U.S. Patent No. 11,170,130), which outlines innovative methods for storing user profile data in a distributed database for anonymous verification. In simple terms, this system encrypts and distributes user data across multiple locations, enabling secure, anonymous verification without exposing the underlying data.
Aster Key’s unique “Triple-Masked Data” approach incorporates three layers of security:
- End-to-End Encryption – Ensures secure transmission of data between parties.
- Identity Stripping – Separates personal identifiers from financial data.
- Blockchain Verification Proofs – While not yet in production (pending lender readiness), Aster Key uses blockchain technology to verify data integrity without exposing the data itself. We believe that in the near future, lenders can rely on cryptographic proofs instead of storing sensitive data—accelerating workflows while managing regulatory requirements in parallel.
Aster Key:
The Future of Secure Lending
Secure Financial Profile
Borrowers create a secure financial profile within the lender’s Aster Key–secured app. They decide when and how to engage — starting conversations or applications without exposing all their data.
Built on Trust
This trust-first approach gives borrowers confidence in their lender from day one. Privacy is respected before anything is shared.
Share Only When Ready
Borrowers share encrypted, verified data only when ready — with no central servers, no data mixing, and no easy targets for hackers.
Testimonials
Aster Key remakes lending to everyone’s advantage

